In part 1 of our series on quantum computing, we were introduced to quantum mechanics and how it surpasses traditional computing, using qubits for faster and more complex problem-solving. Recent advancements, like IBM’s increasingly powerful processors, open new possibilities in various fields and threaten current encryption methods. This has prompted the development of quantum-resistant algorithms to protect digital security, demonstrating the technology’s potential and challenges.
Lattice-Based Cryptography: The Bedrock of Quantum Defense
Lattice-based cryptography is heralded as one of the most promising and versatile approaches for constructing quantum-resistant algorithms. But what exactly are lattices in a cryptographic context?
Lattices: The Infinite Checkerboard of Protection
To understand lattices, let’s picture an endless grid of evenly spaced points, like a checkerboard extending infinitely in every direction. Now, imagine this checkerboard isn’t just on a flat surface but extends up and down and into dimensions beyond our three-dimensional world — it gets pretty hard to visualize!
Lattices in the cryptographic context are similar to these multidimensional grids. The security of lattice-based cryptography comes from specific problems that are easy to do one way but very hard to do the opposite way – especially in these higher dimensions. For example, if each point on the grid represents a possible solution to a problem, finding the shortest path between two points on a 2D checkerboard is relatively easy. But in a high-dimensional lattice with billions upon billions of points, finding this shortest path becomes mind-bogglingly complex, much like an interstellar maze with countless routes.
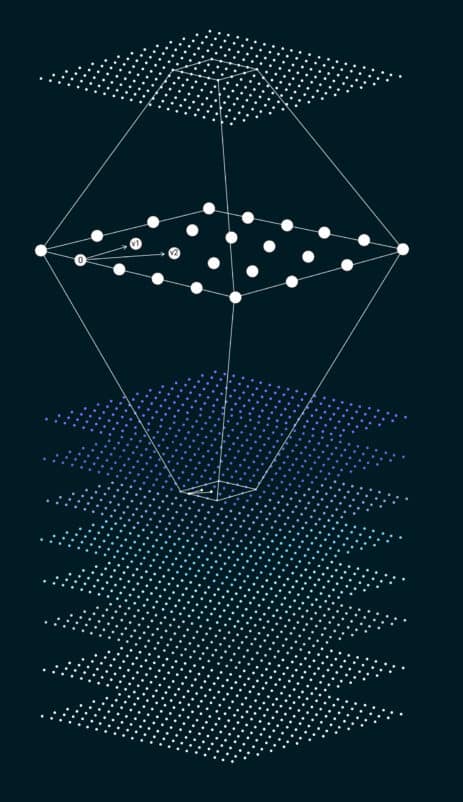
Quantum computers, which are exceptional at solving certain types of problems, still struggle with these lattice problems because of their complexity. That’s why cryptographers are excited about them; lattices could secure information that even quantum computers can’t crack – ensuring that our digital communications remain safe and private even as technology advances.
Extend Your Understanding – Lattice-based cryptography is based on problems generally considered hard to solve – they are known as NP-hard. This means no fast solution is known for these math problems, making them tough for both classical and quantum computers. Specifically, problems like the shortest vector problem (SVP) and the closest vector problem (CVP) are used in lattice cryptography because they are hard in both average and worst-case scenarios, making cryptographic systems built on them very secure.
Quantum-Safe Cryptography: Current Strategies
Protecting cryptographic systems against quantum computer threats hinges on two key concepts: Quantum Key Distribution (QKD) and Post-Quantum Cryptography (PQC).
- Quantum Key Distribution (QKD): This technique creates private symmetric keys via quantum and classical channels, such as optical fibers. Well-known protocols like BB84 use quantum mechanics to guarantee that any interception will corrupt the key and reveal the eavesdropper, thereby preserving security. Despite successful implementations since 2003, QKD is not fully scalable, with ground-based and satellite exchange limitations due to quantum state degradation and infrastructure demands. It’s not a feasible option for blockchain security now, but it may become viable as technology progresses.
- Post-Quantum Cryptography (PQC): Unlike QKD, PQC employs complex mathematical problems to generate secure, quantum-resistant asymmetric keys using only classical processes. The focus is on hash-based, code-based, lattice-based, and multivariate cryptography categories.
Securing the Future: The Vanguard of Quantum-Safe Algorithms
In an era where quantum computing threatens cryptographic norms, the National Institute of Standards and Technology (NIST) has spearheaded the charge to future-proof digital security. Identifying the need for quantum-resistant algorithms, NIST has meticulously shortlisted a cadre of cutting-edge cryptographic candidates designed to shield our data against the quantum threat.
NIST started a standardization process for post-quantum algorithms in 2016, resulting in the following selected algorithms:
- KEM Category:
- Crystals-Kyber, utilizing algebraic lattices for key encapsulation.
- Digital Signature Category:
- Crystals-Dilithium, with algebraic lattices for signatures.
- Falcon, a lattice-based algorithm incorporating SHAKE256 hashing.
- SPHINCS+, a stateless hash-based signature scheme.
Blockchain in Quantum Crosshairs: Protecting Digital Assets
Cryptocurrencies and blockchain teeter on the brink of vulnerability with the advent of quantum computing. Cryptographic algorithms, like the Elliptic Curve Digital Signature Algorithm (ECDSA), stand on mathematically complex problems that quantum computers can solve with startling efficiency. PQC aims to fortify digital assets against quantum onslaught, crafting cryptographic ciphers that even quantum juggernauts can’t easily assail.
Quantum Resilience: Bitcoin’s Defensive Shift
Theoretically, quantum behemoths could ‘steal’ Bitcoin through decryption, exposing private keys from public ones. Albeit a distant prospect now, the Bitcoin and cryptocurrency communities are not taking chances due to the sheer magnitude of qubits and error correction needed. They’re advocating for a shift to quantum-resistant protocols, even though such a transition requires deep consensus, a taxing endeavor given the decentralized essence of these networks.
Quantum-Safe Infrastructure: Global Strategies for Digital Security
Updating existing digital infrastructure to be quantum-resistant requires a cohesive effort that merges policy, research, and practical implementation:
- Consensus and Standardization: There’s a critical need for global consensus on standards for cryptographic protocols, necessitating collaboration for validation and international agreement.
- R&D and Performance: Intense research to develop efficient quantum-resistant algorithms must balance heightened security with practical performance in various applications.
- System Upgrade: Introducing and integrating these new algorithms requires compatibility with old and new systems without causing operational disruption.
- Knowledge and Enforcement: This change mandates broad education on the urgency of quantum-safe practices, while regulatory bodies must craft policies that foster a smooth transition.
- Investment in Innovation: Resources, both human and financial, are imperative for the research, testing, and implementation of secure cryptographic measures.
- Future-proofing and Collaboration: Quantum-resistant algorithms must be flexible to adapt to ongoing technical advancements, verified through extensive testing to ensure durability against quantum attacks. Additionally, global cooperation is needed to align security practices across nations with diverse interests and capabilities.
Embracing the Quantum Leap: A Future Forged with Foresight
As we stand on the periphery of the dawning age of quantum computing, there’s a palpable sense of excitement and anticipation. Current conversations may overstate its short-term significance yet underplay its long-term implications.
While its evolution may seem slow to critics, with few tangible breakthroughs seen as progress markers, many large organizations and governments continue to invest heavily in this field. Constructing a functional quantum computer involves overcoming herculean challenges, making it unlikely for a random hacker to leverage this technology against current cybersecurity measures. However, the potential for nation-states to employ it for cyber warfare cannot be dismissed.
Awareness of security vulnerabilities and strategic countermeasures becomes our guiding light, enabling a harmonious balance between the excitement of exploration and the necessity for protection. Our collective leap into the quantum era must champion both human ambition and unwavering cybersecurity.





